TL;DR: a YouTube ad led to a video peddling a fake Among Us mod for iOS, but is a cover for a possible ad revenue “click fraud” scheme.
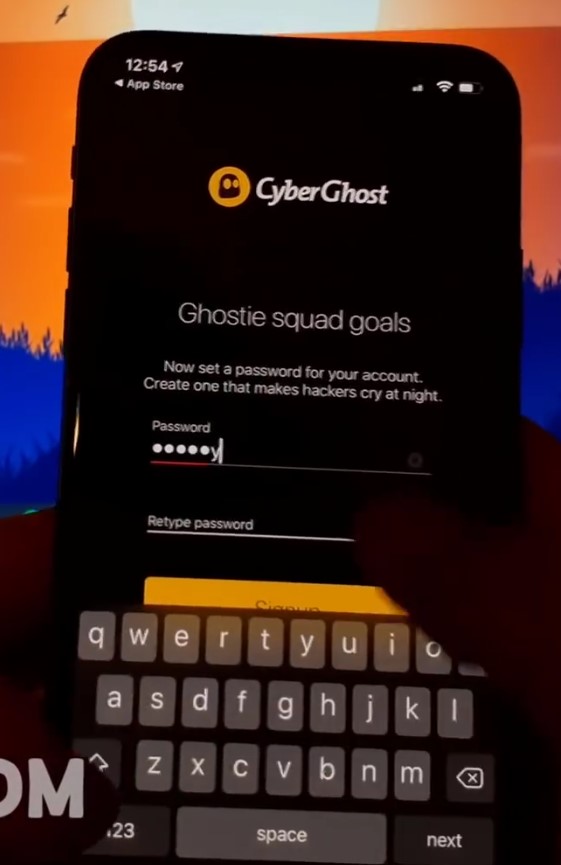
On this particular night when browsing recommended content in my iPhone’s YouTube app, I was shown an advertisement that promised the user a “modded” version of the current-hype AmongUs game. Out of curiosity, I tapped on the ad and watched the linked YouTube video. A modicum of common sense is enough to determine that this ad revolved around some sort of scam or revenue scheme otherwise; the linked YouTube video is unlisted and was only visible by visiting the link presented by the aforementioned inline advertisement. I pulled down a copy of this video in case the original poster, or YouTube, takes the video offline:
The video starts out with what appears to be a demo of the Among Us game running on a newer-model iPhone (model X or newer?). In this demo, the user appears to be controlling their game’s character in a typical fashion, except the player’s character is moving significantly faster in the game than is typical. Of note about this demo, though, is the joystick feature in the bottom left corner of the device’s screen, where the thumb of the person “playing” the game appears to only be mimicking real game play. There are multiple instances, if you watch closely, where the joystick on the screen does not align with the user’s thumb tip or the position, which leads to the impression that the user’s phone is merely showing a (potentially doctored) video. Another element of note is that if the video is truly in play on the user’s phone, touch interactions with the screen should show the video playback interface, but a closer look at the user’s finger positioning and movements indicate that the user is avoiding making contact with the device’s screen to avoid precisely this. Clever positioning of the user’s hands, the phone, and the location of the camera capturing the video likely conceals this touch-avoidance. One last detail is the small overlay image of The Joker’s face (the Heath Ledger version from The Dark Knight), which moves to a different part of the screen in this first scene. It is suspected that this image is a sort of watermark for the video being played, or perhaps a cue for the “actor” in this video; the true purpose of this image is unknown based on the video’s contents. A transition cuts the video to the next scene, where the narrator and user (two different individuals, it is presumed) “demonstrates” the process of obtaining the purported game mod.
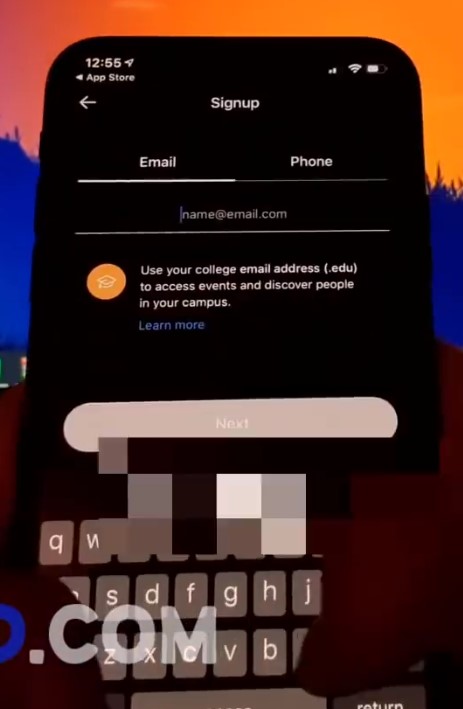
The next scene starts with the user device presenting the “amongmod[.]com” website in the browser (archive.org mirror), with the narrator directing the viewer to visit this site to obtain the mod. In the background, the user’s Windows 10 desktop is visible with the tray clock indicating a date of “11.10.20;” the exact year is cut off but it is assumed the date of this recording is 11 October 2020. The viewer is directed to tap the presented “Download Now” button on this webpage, where a mobile device configuration “profile” is downloaded to the device. A copy of this profile is available here for further analysis: (archive.org mirrored copy).
This author, of course, strongly advises against installing mobile device profiles without a known, vetted purpose such as for app development purposes or corporate application/internal site access. There are known incidents of malicious actors using profiles to surveil and manipulate mobile device activity, and users should not be so eager to install profiles such as in this instance.
A query of the domain’s whois and DNS records at the time of this writing is as follows:
whois amongmod[.]com
Domain name: amongmod[.]com
Registry Domain ID: 2564632260_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.namecheap.com
Registrar URL: http://www.namecheap.com
Updated Date: 0001-01-01T00:00:00.00Z
Creation Date: 2020-10-08T18:02:24.00Z
Registrar Registration Expiration Date: 2021-10-08T18:02:24.00Z
Registrar: NAMECHEAP INC
Registrar IANA ID: 1068
Registrar Abuse Contact Email: abuse@namecheap.com
Registrar Abuse Contact Phone: +1.6613102107
Reseller: NAMECHEAP INC
Domain Status: clientTransferProhibited https://icann.org/epp#clientTransferProhibited
Registry Registrant ID:
Registrant Name: WhoisGuard Protected
Registrant Organization: WhoisGuard, Inc.
Registrant Street: P.O. Box 0823-03411
Registrant City: Panama
Registrant State/Province: Panama
Registrant Postal Code:
Registrant Country: PA
Registrant Phone: +507.8365503
Registrant Phone Ext:
Registrant Fax: +51.17057182
Registrant Fax Ext:
Registrant Email: b4806f7d6aff4c3f982ff5e67abd85a6.protect@whoisguard.comnslookup -q=any amongmod[.]com
Non-authoritative answer:
amongmod[.]com text = "v=spf1 +a +mx +ip4:54.39.49.75 ~all"
amongmod[.]com
origin = ns13.hoststage.net
mail addr = monitoring.host-stage.net
serial = 2020100803
refresh = 3600
retry = 1800
expire = 1209600
minimum = 86400
amongmod[.]com nameserver = ns13.hoststage.net.
amongmod[.]com nameserver = ns14.hoststage.net.
Name: amongmod[.]com
Address: 144.217.221.149
amongmod[.]com mail exchanger = 0 amongmod[.]com.From these results, we gather that the owner of the target site’s domain name is hidden behind a domain name privacy proxy, which itself isn’t unusual or suspicious, but doesn’t yield any further useful information about the owner. Of note, though, is the domain name’s creation date, listed as 8 October 2020. Additionally, the DNS lookup results show that the site is being served by a provider named HostStage. An additional whois lookup of the returned website and email server IP addresses indicate that the site is being provided from infrastructure owned by the French web hosting company, OVH.
The subject website was visited on a desktop computer with the browser configured to imitate an Apple iPhone running the iOS operating system version 14.0.1. A recording of the website, its network activity, and output of its running code follows:
In short, the subject web site displays a fake progress bar to simulate activity happening on the server-side of the site, and after a period of time the mobile device profile is downloaded. The browser’s network traffic inspector showed that no communication between the end-user and the server actually occurs, confirming the fake progress bar, and a glance at the browser’s web code console shows that the JavaScript handling the progress bar emits a “xD” emote to the browser’s console while running.
Going back to the video, some additional observations were made as the user demonstrates the installation of the downloaded mobile device profile:
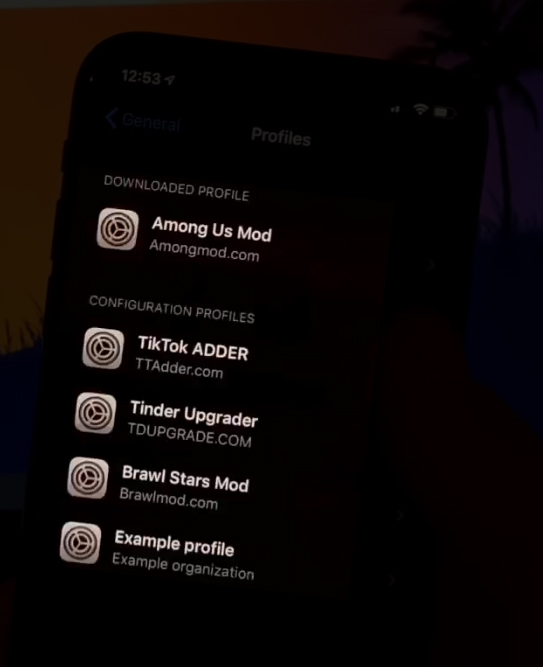

Some additional research into the domains listed on the other profiles installed on the user’s device:
- TTadder[.]com: resolves to 144.217.221.149 (same as above). Domain name registered on 6 February 2020 with the same Namecheap privacy proxy information from above.
- TDUPGRADE[.]COM: resolves to 144.217.221.149 (same as above). Domain name registered on 17 November 2019 with the same Namecheap privacy proxy information from above.
- Brawlmod[.]com: domain is not resolving to an IP address at the time of this writing. Domain name registered on 29 April 2020 with the same Namecheap privacy proxy information from above. Of note, the two name servers returned in the whois lookup results are listed as “ns1[.]virused[.]host” and “ns2[.]virused[.]host.” These nameservers themselves are not resolvable at the time of this writing and it is suspected that these name servers were set by the registrar as a result of a malicious activity complaint against the domain registrant.
The video continues on to demonstrate the “install” process following the installation of the given mobile device profile. The profile inserts a home screen icon for what Apple calls a WebClip. The installed profile adds the “mod” icon to the device’s home screen, using an embedded PNG image and a WebClip flagged as full screen and non-removable by the user. Apple’s documentation states that any WebClip installed by a profile with the non-removable flag is only removable by uninstalling the related mobile device profile. The profile installed here links to a subdirectory of the amongmod[.]com website. (archive.org mirrored copy) The video’s narrator indicates that the mod must install some “important updates” when opening the “mod” for the first time. (“It’s completely normal so just click the button Update Now and follow the given steps. After you do it, you will instantly be able to use this mod.”)
Upon tapping the “Update Now” button on the full-screen WebClip, the user is sent to the locked1[.]com site as indicated by the now-visible browser URL bar at the top of the screen. This process was performed on a desktop browser, configured the same as before to simulate a mobile device, to further analyze the background network activity:
While the video narration states that updates must be installed to utilize the Among Us game mod, the true purpose of the “updates” (and aforementioned locked1[.]com website) is to persuade the user into installing applications linked by the presented site. (“…it’s necessary because needs these apps to work properly.”) Three apps are presented on the page. Upon tapping one of the links, the user’s device will redirect them to the Apple App Store to install the targeted application, and the narration says that user’s need to use each app for at least 30 seconds. (“30 seconds is enough time to let the game take the necessary stuff from the app.”)
It is presumed that the stated “30 second” timeframe is given to indicate to whatever backend analytics/promotion tracking system that there is an “active” user with the given app, similar to the minimum view times that YouTube dictates with video advertisements to discern whether an impression (or “view”) actually occurred for the advertisement. The video’s narrator also says that the given timeframe “will give the updater enough time to finish the process,” which is a cover for the 30 seconds required for the app to be considered “active.” I suspect that the true purpose of this scheme is to make money from referrals or advertisements of apps, requiring new accounts or “installs” to occur to yield a payment for the referral or ad. By persuading users to install targeted applications and use them for the minimum of 30 seconds, the scheme operators yield a payment of some form for the referral to said app.
The video goes on to inform viewers that after completing this process for two apps, if the “updater” page (the locked1[.]com site) does not indicate completion, the user “did something wrong” and they should “try one more app;” the displayed web page also indicates this and suggests that the user “try again with different Apps.” (capitalization as displayed on the locked1[.]com site) There is a potential that the referral/advertising/analytics processing built into these targeted, installed apps isn’t 100% accurate or flawless and may result in a failed “acknowledgement” of an active install or user. Additionally, the persuasion for users to install a third app may be artificial and is designed to coerce users into completing three installs (or “referrals”); some may consider this to be an advertising trick related to artificial scarcity or manufactured urgency.
The video concludes with the completion of the mod’s “updater” process and the launch of the Among Us game. Upon close review of the user’s interactions with the device, there are noticeable discrepancies with the user’s finger movements and what is displayed on the screen, suggesting that the WebClip installed by the mobile device profile is playing back a video. Specifically, the “cheat menu” displayed in the “modded” app doesn’t align with all of the actor’s taps and scroll gestures and at one point, the actor attempts to conceal this by frantically tapping a menu item to try matching what is displayed on the screen.
One more note regarding the locked1[.]com site: whois lookup results for this domain name share the same indicators as all of the previously discussed domain names, except this site’s listed name servers point to Amazon Web Services (AWS); the domain name resolves to IP address 3.225.87.211 which is, indeed, registered to AWS. When visiting this IP address directly in a web browser, a certificate mismatch error is presented since the site’s SSL certificate does not list the given IP address as the site the certificate is issued to. Furthermore, the presented certificate indicates that it was issued for the “appregistration[.]net” domain; the whois record for this domain also share all of the indicators for the domains discussed previously and, overall, indicates a shared operator for all of these sites and the underlying advertising/referral schemes. A quick query of the Shodan database also shows a SSL certificate associated with this site, but specifies “mobileoasis[.]net” as the assigned website and not the discovered appregistration[.]net domain name. Of course, the whois records for this site also shares the same information as the sites already discussed.
Lastly, a quick web search of the appregistration[.] domain led to some direct links to the site, revealing subdirectories and other active advertising/referral campaigns:


With the subdirectory names of “filelockers” and “contentlockers,” I think I’ve potentially discovered the names associated with these activities. If these are already well-established categories or names then I’ll admit that it’s new to me! A quick peek at the site source code for these pages found a curious indicator as to who may be operating these schemes:

This rabbit hole needs to stop getting deeper, so I’ll end with this: one of the first web search results for “mobverify” led me to a GitHub repository, listing a repository owner named MobClub of Shanghai, China. This is worth more research, I think.
PS: my thanks to Milan Boers for a quick way to pull down a copy of a GitHub user’s entire repository!